STEP 6: FS - Creating both sides of the federation trust
To do this, we have to perform 5 simple steps: export the policy from the account domain, import the policy in the resource domain, create the claim mapping in the resource domain, export the partner policy in the resource domain and import that policy in the account domain.
A) Export the Trust policy (Account domain)
1. Open Active Directory Federation Services and right-click the Trust Policy to Export Basic Partner Policy and safe it to any location.
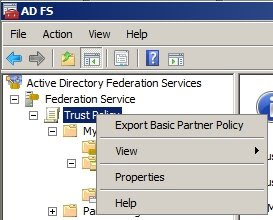
2. E-mail the XML file to the administrator of the Resource domain
B) Import the Trust policy (Resource domain)
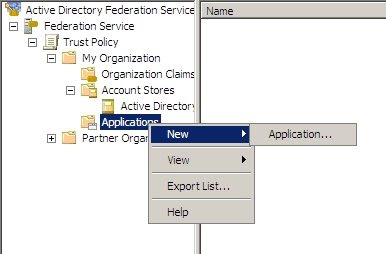
1. Open Active Directory Federation Services and browse to Trust Policy --> Partner Organizations and right click Account Partners to add a new Account Partner.
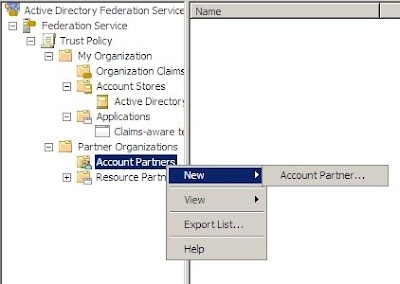
2. In the wizard, browse to the XML file you received from the partner and check if the details displayed are correct.
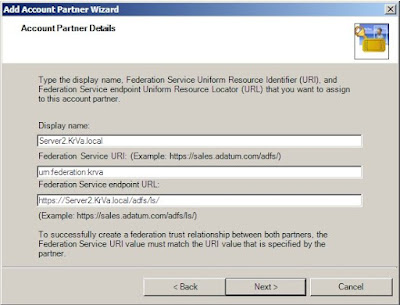
3. Then, select to Use the verification certificate in the import policy file before continuing.
4. If you are setting up FS between 2 forests that do not have a trust configured between them, select Federated Web SSO and click Next.
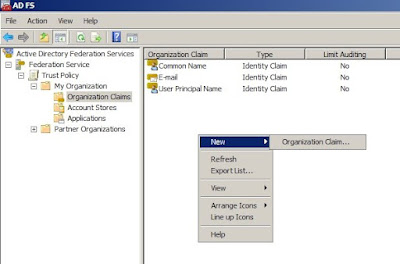
5. In the Identity claims option, select UPN claim and E-mail claim, after which you provide DNS suffixes and Enable this account partner.
C) Create the claim mapping (Resource domain)
1. Open Active Directory Federation Services and browse to Trust Policy --> Partner Organizations --> Account Partners and right-click the partner to add a new Incoming Group Claim Mapping.
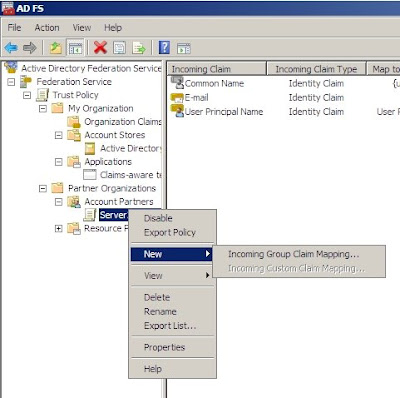
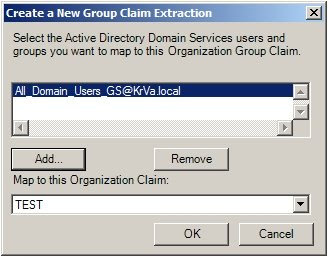
2. Enter a name and make sure you select the correct organization group chain (in this case, there is only one)
D) Export the Partner policy (Resource domain)
1. Open Active Directory Federation Services and browse to Trust Policy --> Partner Organizations --> Account Partners and right-click the partner to Export Partner Policy and safe it to any location.
2. E-mail the XML file to the administrator of the Resource domain
E) Import the Partner policy (Account domain)
1. Open Active Directory Federation Services and browse to Trust Policy --> Partner Organizations and right click Resource Partners to add a new Resource Partner.
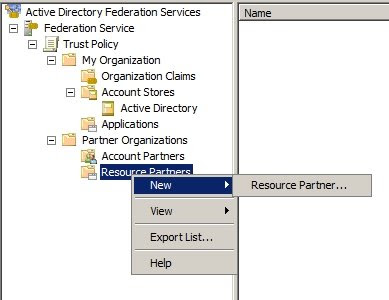
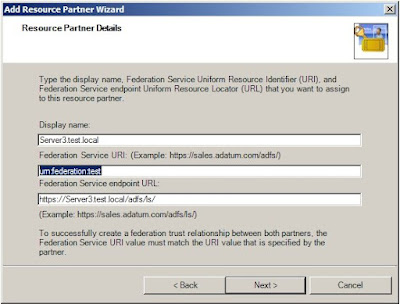
2. In the wizard, browse to the XML file you received from the partner and check if the details displayed are correct.
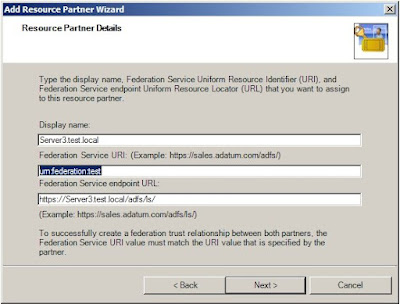
3. If you are setting up FS between 2 forests that do not have a trust configured between them, select Federated Web SSO and click Next.
4. In the Identity claims option, select UPN claim and E-mail claim, and verify that the DNS suffixes are adding the DNS suffix of the Account Domain.
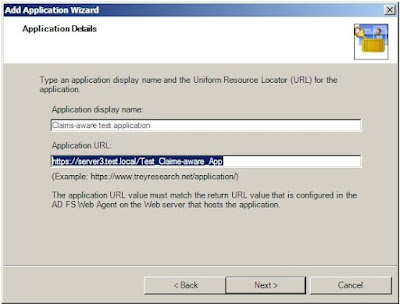
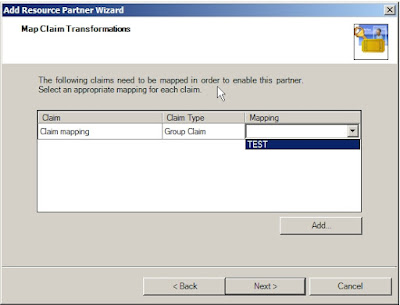
5. On the Map Claim Transformations page, under Mapping select the ClaimApp Claim (TEST in my case), then click Next and select to Enable this resource partner.
There, that’s it. As promised, it was quite a long way. But now that it's working, it feels pretty good doing stuff that not too many other people do, am I right? :)
If you are having problems, to troubleshoot check that:
1. the client PC has the DNS IP-adresses of the DNS servers in both domains configured
2. the FS servers have been added to the trusted sites of the local intranet in your internet explorer
3. if you are setting this up in a test environment, make sure the routing between both domains is working.
Federation Services setup posts:
1. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 1: Overview and installation
2. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 2: Configure IIS to use SSL on the FS servers
3. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 3: Configure the FS certificates
4. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 4: Configuring the FS server in the Account domain
5. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 5: Configuring the FS server in the Resource domain